
Spring Security OAuth is deprecated, and many of us wonder what to use as an alternative.
Security fixes for the deprecated project will be supported until May 2022,
so we have time to wait for the recently announced Spring Authorization Server,
or we can migrate to one of the plenty of authorization servers available today.
In this tutorial, we are going to look at how to migrate from Spring Security OAuth to Keycloak.
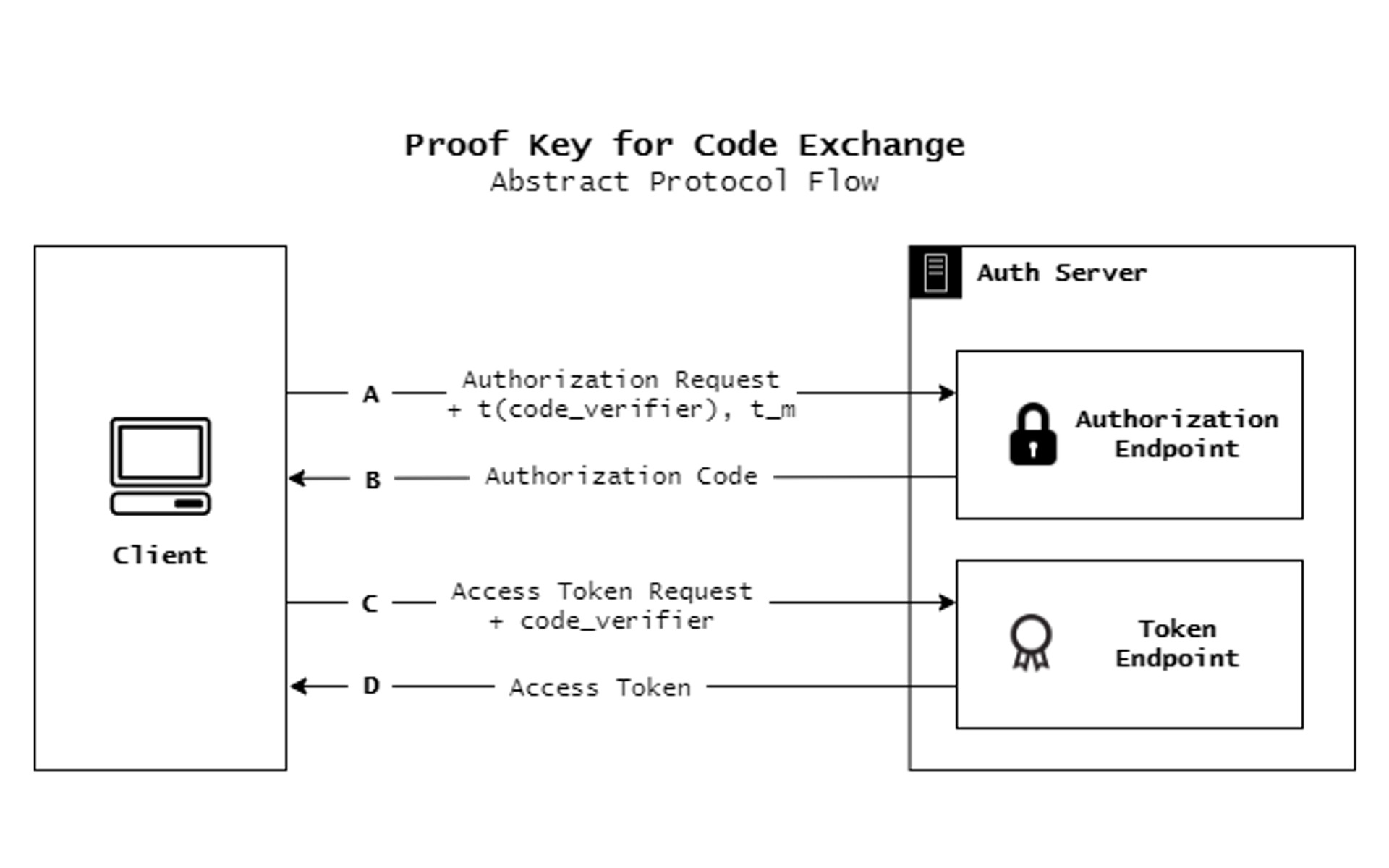
RFC 7636: Proof Key for Code Exchange (PKCE, pronounced “pixy”) describes an extension to the Authorization Code flow to protect public clients from authorization code interception attack.
In this tutorial, we are going to look at how to implement this extension in an OAuth 2.0 authorization server built using Spring Security OAuth, which does not support it out of the box.

Load balancing is the process of distributing network traffic between multiple servers,
used to improve the performance and reliability of websites, applications, databases and other services.
Using a centralized load balancer is the most traditional approach for this, but client-side load balancing still has some advantages and is also quite common.
In this tutorial, we are going to look at how to implement client-side load balancing in gRPC Java client.

Rejoiner is a fairly young framework with the goal of bringing together two powerful and increasingly popular technologies, GraphQL and gRPC.
It creates a unified GraphQL schema for gRPC microservices and provides DSL to modify it.
In this tutorial, we are going to create several gRPC microservices and see how we can use Rejoiner to expose them via a single GraphQL API.
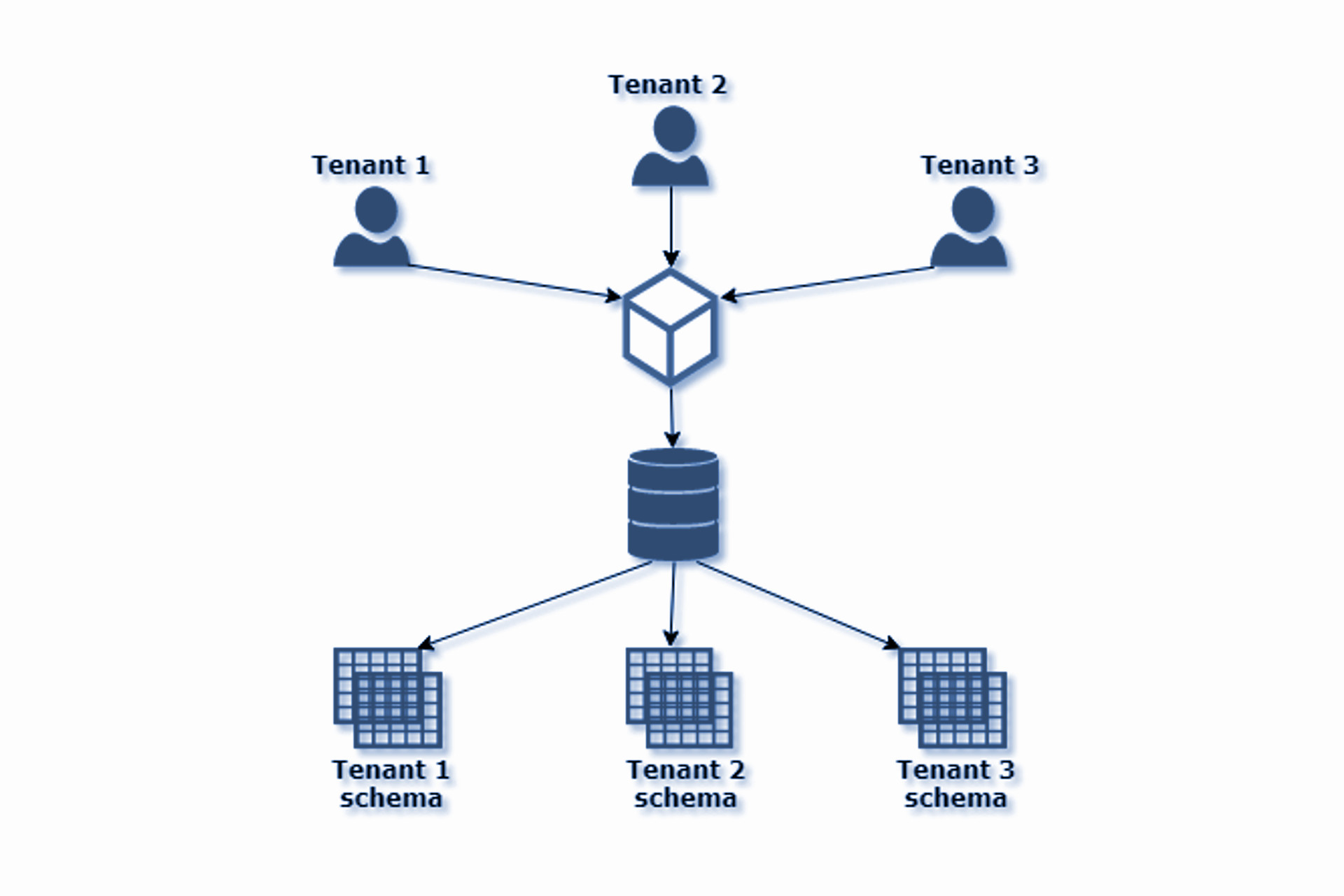
Multi-tenancy is an architectural pattern that allows multiple tenants to use a single instance of software,
the purpose of which is to provide each tenant with a dedicated share of the instance but to isolate the information belonging to each tenant.
In this tutorial, we are going to look at how to implement schema-based multi-tenancy in Spring Boot application.

Column-level encryption is one of the database encryption methods, which allows user to select specific attributes
for encryption instead of encrypting the entire database.
In this tutorial, we are going to look at how to implement database column-level encryption with Spring Data JPA.





