In modern software, complex tasks often exceed the capabilities of a single AI agent—autonomous entities designed to perform specific tasks.
Collaborative multi-agent systems enable these agents to work together, leveraging their unique specializations, sharing context, and dynamically tackling problems that single agents can’t manage alone.
In this tutorial, we’ll create a multi-agent system using LangChain4j and Spring State Machine, showcasing how agents can interact, share memory, and delegate tasks efficiently.

In the world of service communication, gRPC serves as a common choice for internal interactions, while REST and GraphQL act as the go-to options for exposing external APIs.
When these technologies are combined, there arises a need to seamlessly map streaming RPC to reactive stream publishers, which are integral components of reactive REST endpoints and GraphQL subscriptions.
In this tutorial, we will explore the implementation of this mapping, bridging the gap between gRPC streaming and reactive streams.

gRPC builds on HTTP/2’s long-lived connections which provides a foundation for long-lived, real-time communication streams
and allows gRPC to support multiple communication patterns, one of which is server streaming RPC.
One use case for server streaming RPC could be to implement long-lived streaming of events or notifications from the server to interested clients,
and in this tutorial, we are going to look at how to implement this with gRPC Java using observer pattern.

We may run into the need to inject Spring Beans into JPA entities or some other unmanaged objects,
which could be an indication that we need to rethink our architecture, but sometimes this cannot be avoided.
It is possible to do this using @Configurable annotation,
but for this to work, the annotated types must be woven with the AspectJ weaver.
In this tutorial, we are going to look at an alternative way to access Spring-managed components from unmanaged objects that is arguably better than injection.

The Saga pattern is a way to maintain data consistency in distributed systems by sacrificing atomicity and relying on eventual consistency.
A saga is a sequence of transactions that update each service, and if at some stage it fails, it performs compensating transactions that counteract the previous stages.
There are two common saga implementation approaches - choreography and orchestration.
In this tutorial, we are going to look at how to implement orchestration-based saga using Cadence Workflow.
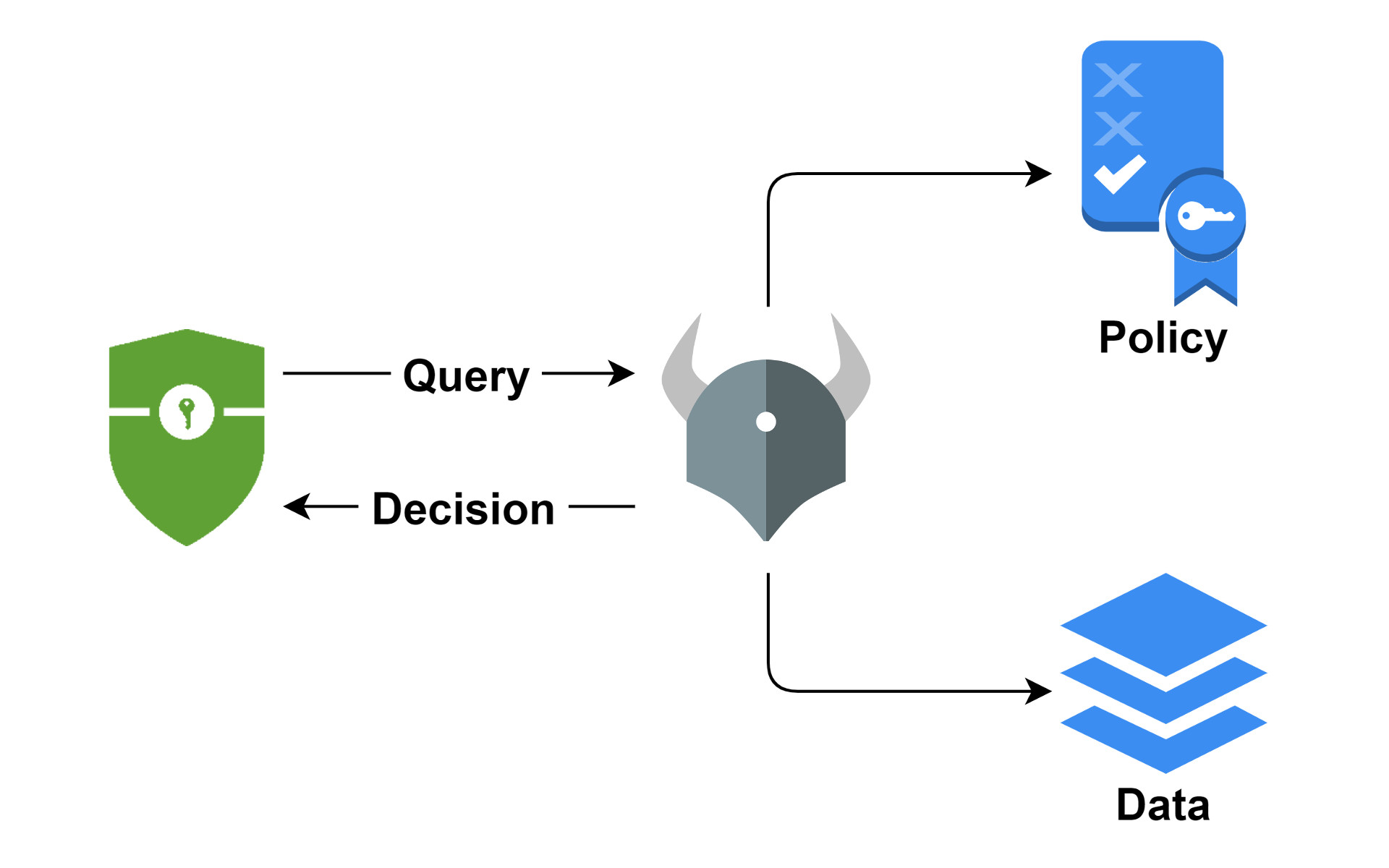
While OAuth2 and OIDC have become the de-facto standard for authentication and are very popular,
existing authorization standards (e.g. XACML, UMA) are difficult to implement and even use,
so developers continue to roll their own solutions, which is time-consuming and increases maintenance costs.
In this tutorial, we are going to look at how to simplify authorization by externalizing access control decisions using Open Policy Agent and Spring Security.






